COVID-19 will leave a mark on history as a transformative event in the 21st century. From a technological perspective, it forced governments, enterprises and individuals around the world to rethink and adjust how people live, work and play. Those entities and individuals that have accelerated the use of technology, modified their business models and upskilled their talents have allowed them to survive and thive in the post-COVID era.
With the benefits of higher agility, scalability, cost-efficiency and risk reduction, the cloud has become an indispensable tool for business transformation. According to IDC’s European Multicloud Survey, 2021, about 46 percent of European organizations said they “currently use any cloud computing technologies extensively,” and more than 36 percent of their infrastructure spend is dedicated to the public cloud—higher than their core datacenter infrastructure spend.
Geo-political considerations on cloud adoption
While cloud adoption is prevalent across the world, there is a growing business and political concern about digital sovereignty. Today, the World Economic Forum estimates that over 92 percent of all data in the Western world is stored on servers owned by US-based companies. Governments and regulated industries around the world are increasingly aware and concerned about their dependence on cloud service providers that are under the purview of laws and regulations separate from their own. Foreign governments may scrutinize these data under national security or surveillance laws. In the US, the government may conduct surveillance and investigation of electronic communication media, including the internet. These concerns are largely shaped by four pieces of legislation:
- FISA (Foreign Intelligence Surveillance Act) 1978 Amendments Act of 2008
- Enacted in 1978—before the proliferation of the internet.
- Section 702 is part of the Foreign Intelligence Surveillance Act added as an amendment in 2008. It allows intelligence agencies to collect foreign intelligence from non-Americans located outside the United States.
- USA PATRIOT Act (Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism Act) 2011
- Enacted shortly after the September 11, 2001 terrorist attacks
- Expired in 2015 but renewed through the Freedom Act
- A report showed that by 2014, out of over 11,000 sneak-and-peak warrant requests, only 0.5% were used for terrorism.
- USA FREEDOM Act (Uniting and Strengthening America by Fulfilling Rights and Ending Eavesdropping, Dragnet-collection and Online Monitoring Act) 2015
- The Freedom Act extends many of the would-be expired provisions of the Patriot Act, but with more limitations due to public scrutiny in the wake of the Edward Snowden revelations (2014) regarding bulk surveillance and interception.
- Renewed many of those expiring provisions of USA Patriot Act through 2019, albeit with some new limits concerning bulk interception on telecommunication metadata about US citizens.
- CLOUD Act (Clarifying Lawful Overseas Use of Data Act) 2018
- Amends two titles of the existing Electronic Communications Privacy Act (ECPA)
- Requires providers of electronic communication service or remote computing service to preserve and disclose communications and records under subpoena orders
While most cloud users are law-abiding entities, these surveillance laws have deterred some from trusting the cloud more, as privacy protection is considered a fundamental right that should not be compromised. Against this backdrop, digital sovereignty has become an important technological concern.
What is digital sovereignty?
In simple terms, digital sovereignty refers to the ability to have control over your digital destiny. Gartner elaborates the three pillars of digital sovereignty as:
- Data sovereignty confers that information is subject to the rules of its originating jurisdiction (regardless of its actual location).
- Operational sovereignty is the degree to which a customer organization has transparency and control over the provider’s operations.
- Technological sovereignty is the degree to which a customer organization can ensure the continuity and control of its rights to technical autonomy.
In effect, Digital Sovereignty translates into several business benefits. Data sovereignty allows users to retain control of their data, including location and movement of data, and data protection mechanisms such as cryptographic management, thereby keeping data within customers’ jurisdiction and avoiding subpoena threats or geo-political impacts. Operational sovereignty enables users to restrict and control access, thereby avoiding unauthorized access by privileged users and cloud service provider admins. Technological sovereignty facilitates multi-cloud operation, thereby avoiding vendor lock-in. It is worth noting that correctly exercising digital sovereignty can bolster customer confidence in migrating to the cloud and reap tangible financial returns, such as an ROI of 193 percent within six months.
Data encryption in the cloud
Regardless of the cloud service offering (IaaS, PaaS, SaaS), organizations deploying their workload in the cloud are ultimately responsible for the security of their data, as explained in the shared responsibility model. Encryption is the common and trusted mechanism to protect data at rest and in transit. While encryption itself is straightforward, the secure management of the cryptographic keys (from generation to sharing, usage, storage, rotation and revocation of the keys) can be challenging, especially when multiple users operate multiple applications with multiple workloads, and the keys need to be rotated frequently.
Traditionally, some service providers, storage or database application vendors have taken a simple approach of storing the cryptographic keys with the encrypted data. While this practice certainly allows efficient access to the keys by the applications, this approach will not be able to fend off unsophisticated hacking attacks nor demonstrate segregation of duties, which is a key deterrent of insider threats. As a result, various legislations and guidelines have been published to facilitate how cloud users shall exert digital sovereignty over their own data.
These publishers include those in government-related establishments in Europe, Hong Kong, India, Japan, Singapore, and industry-standard setting bodies such as Cloud Security Alliance. The common requirement of these regulatory compliances is for the data controllers to be solely responsible for the management and control of the cryptographic keys. The objective is to restrict access by non-authorized entities, such as the cloud service providers or foreign governments, and that they are able to access the data only with explicit consent of the data controllers.
How is digital sovereignty maintained in the cloud?
While the public cloud can meet most of the business needs of general users, we have seen that some users (especially those in the government sectors, regulated industries and those that are more security conscious) will demand a higher level of assurance that they will retain digital sovereignty over their data. In fact, IDC top predictions for security and trust in 2023 and beyond indicates that by the end of 2025, 40 percent of major enterprises will mandate data sovereignty controls from their cloud service providers to adhere to data protection and privacy regulatory requirements. Below are some additional measures cloud providers and enterprises undertake, sometimes using combinations, to uphold their customers’ digital sovereignty.
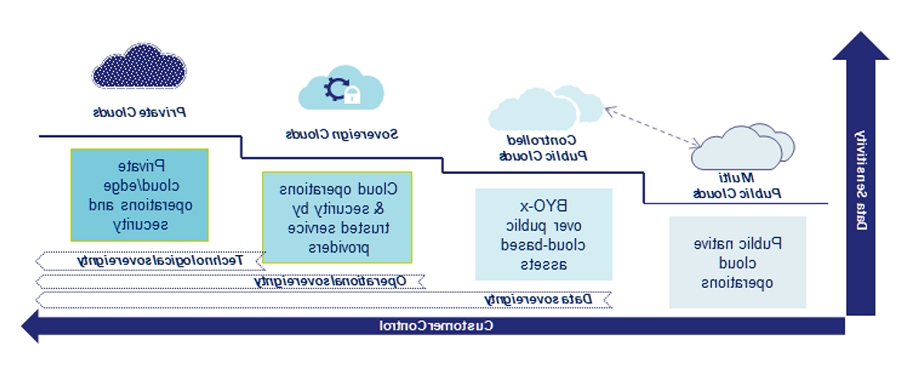
- Controlled Public Clouds: Guardrails deployed in clouds allow organizations to retain jurisdictional control over their data to ensure data residency. Control over the access of data, a key component of data security, is critical in protecting sensitive data, where cryptographic technology, process and policy enforcement play a critical role. In addition to technical controls, contractual commitment to demonstrate regulatory and compliance requirements is equally important. There is another innovative type of controlled cloud driven through the concept of sovereign-by-design. Through the sovereign-by-design approach, the customer not only could control the location of data, but they could also configure the encryption of data at rest and in transit, with the encryption keys managed inside or outside of the cloud. With the use of innovative technology such as confidential computing, this totally blocks the system or operator from accessing data running in the CPU and memory enclave and thus protecting data in use. Cloud users requiring an assurance of this level of protection can refer to the relevant compliance certifications as well as reports from external attestation bodies.
- Examples: AWS’ Digital Sovereignty Pledge, Google’s “ On Europe’s Terms,” Microsoft Cloud for Sovereignty are fine examples that allow customers to enhance their sovereignty controls over their data.
- Pros:
- Achieve a reasonable level of data sovereignty through customers’ control of cryptographic key management
- Keep most, if not all, innovation and functionality from public clouds (the workloads still run in public clouds)
- Cons: Local data centers and/or local key management will be needed to fulfil data residency requirements
- Sovereign Clouds: While there are many interpretations of the term, a sovereign cloud usually operates under a joint collaboration between a foreign and a local partner who have controlling stakes of the collaboration and are trusted and authorized entities under the jurisdiction. The collaboration allows provisioning of cloud services within the jurisdiction, meeting data residency requirements and operational autonomy, ensuring that data and infrastructure is protected from control by external jurisdictions and foreign government access.
- Example: S3NS in France, sovereign cloud in Italy, NAVER in Korea, and HTX in Singapore are some of the sovereign clouds being planned and launched to serve clients in their respective countries.
- Pros:
- This will achieve data sovereignty through customers’ control of cryptographic key management, and data residency in-country. With resilience designed and architected from within, organizations can inch closer to the desired independence and operational sovereignty.
- Most innovation/functionality from public clouds are kept depending on the depth of cloud-native functionality implemented by the trusted SP.
- Cons: Since there will be additional procedural, contractual and technological controls that are added in the sovereign cloud while some of the functionalities in native cloud may be removed to fit the operation, customers may be subject to a cost increase against functionality decrease.
- Private Clouds: Data resides in data centers within customers’ control and in-country. Data, operational and technical sovereignty can be achieved to the fullest extent.
- Examples: Government data centers that are yet to migrate to public cloud
- Pros: Maximize the independence from hardware and software vendors, and the ability to exit and port to alternative technologies.
- Cons: Usually reduced functionality and less data for business analytics or machine learning. Also risk of the loss of the breadth and depth provided by the hyperscalers. Building and operating their own data centers can be cost-prohibitive for most organizations.
In the diagram above we see the different hosting models by global hyperscalers or domestic players typically enabling controlled public clouds, sovereign clouds or private clouds operations.
How to realize digital sovereignty technologically?
There are a number of measures that cloud providers can implement to realize digital sovereignty, like data local residency, trust and transparency achieved through third-party attestation, verifiable control over data access, applying guardrails on the workload, etc. Organizations can also work with their cloud service providers to apply additional controls to manage how their sensitive data are encrypted, who has access to their encryption keys, and where those keys are stored and managed. The technical solutions that can achieve the objectives include:
- Bring Your Own Encryption (BYOE)
- Bring Your Own Key (BYOK)
- Hold Your Own Key (HYOK)
Note that BYOE requires installing encryption agents at the operating system/file level and is thus more suitable for Infrastructure as a Service (IaaS) deployment. BYOK and HYOK are applicable to all IaaS, Platform as a Service (PaaS) and Software as a Service (SaaS) deployment models. Examples of BYOK, BYOE and HYOK abound. Users include banks, utilities and SaaS providers such as one of the world’s leading video conference service operators.
How does digital sovereignty meet legislation and industry guidelines?
The Court of Justice of the European Union (CJEU) in its ruling on 16 July 2020 Data Protection Commissioner v. Facebook Ireland LTD, Maximillian Schrems, C-311/18 concluded that appropriate safeguards, enforceable rights and effective legal remedies must be in place before the data are transferred from Europe to the US. Among the technical recommendations, it required that cryptographic keys must be reliably managed and retained solely under the control of the data exporter.
In a separate case involving Doctolib (a healthcare provider), there was a claim filed by the local professional associations and unions that asked for the suspension of Doctolib’s service because the service processed patient records in a public cloud. The basis of the claim was that the cloud in question (AWS Sarl in Luxemburg in this case, which is a subsidiary of a company under US law) may be subject to access requests by US authorities in the framework of US monitoring programs based on Article 702 of the Foreign Intelligence Surveillance Act. On March 12, 2021, the Conseil d’Etat cleared the healthcare provider for using the public cloud, as a number of safeguards have been put in place, including:
- Legal and procedural safeguards: The judge noted that the contract concluded between Doctolib and AWS Sarl provides a specific procedure in the event of an access request by a foreign authority; notably, AWS Sarl guarantees in its contract with Doctolib that it will challenge any general access request from a public authority.
- Technical safeguards: The judge also noted technically the data hosted by AWS Sarl are encrypted and the key is held by a trusted third party in France, not by AWS, to prevent data from being read by third parties.
Conclusion
Cloud users around the world have demanded higher control over their data. The need for control is satisfied by digital sovereignty measures that work collaboratively with cloud providers. This blog post briefly explains how digital sovereignty is achieved in practice and the legal and commercial benefits it brings to cloud users. Governments and enterprises who demonstrate their attention and concern regarding security and privacy will no doubt win the confidence of their citizens and service users.
Editor’s note: Learn about the Certificate of Cloud Auditing Knowledge credential here.
About the author: Welland Chu, Ph.D., CISA, CISM, is the Alliance Director, Asia and Pacific Region at the Cloud Protection & Licensing business line of Thales (cpl.thalesgroup.com). He serves as the Secretary and Vice President of Certification at the ISACA China–Hong Kong Chapter. During his 30 years in the security industry, Chu has led teams of security professionals in assessing and implementing security solutions for clients in the critical infrastructure sector. The author welcomes comments and discussions on the article via email (Welland.Chu@thalesgroup.com). I would would like to thank Siew-Hoon Lim, Ksheerabdhi Krishna, Mukesh Chandak, Romain Deslorieux, for their valuable inputs to this article.